When cracking Active Directory passwords as I explained in this series of blog posts, you can also crack the password history.
The program I’m releasing now will make a report of users who “recycle” their previous passwords by using a common string.
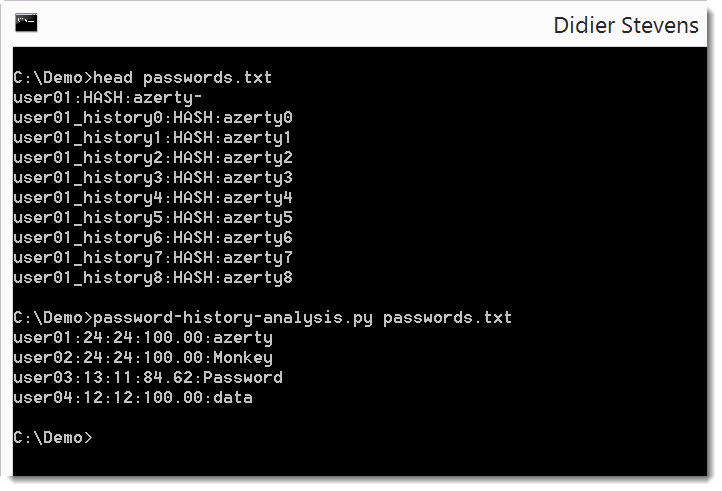
Example:
The man page:
Usage: password-history-analysis.py [options] [[@]file ...]
Program to analyze password history
Arguments:
@file: process each file listed in the text file specified
wildcards are supported
Source code put in the public domain by Didier Stevens, no Copyright
Use at your own risk
https://DidierStevens.com
Options:
--version show program's version number and exit
-h, --help show this help message and exit
-m, --man Print manual
-o OUTPUT, --output=OUTPUT
Output to file
-s SEPARATOR, --separator=SEPARATOR
Separator used in the password files (default :)
-l, --lowercase Convert usernames to lowercase
-n, --nonmatching Print lines that do not match a password entry
-L LENGTH, --length=LENGTH
Minimum length common string
Manual:
This program analyzes files with password history, and reports
statistics on common strings (prefix, suffix, infix) of passwords per
user.
The minimum lenght of a common string is 3 characters by default. Use
option -L to change the minimum length of the common string.
Example of input file (passwords.txt):
user01:HASH:azerty-
user01_history0:HASH:azerty0
user01_history1:HASH:azerty1
user01_history2:HASH:azerty2
user01_history3:HASH:azerty3
user01_history4:HASH:azerty4
user01_history5:HASH:azerty5
user01_history6:HASH:azerty6
user01_history7:HASH:azerty7
user01_history8:HASH:azerty8
user01_history9:HASH:azerty9
user01_history10:HASH:azerty10
user01_history11:HASH:azerty11
user01_history12:HASH:azerty12
user01_history13:HASH:azerty13
user01_history14:HASH:azerty14
user01_history15:HASH:azerty15
user01_history16:HASH:azerty16
user01_history17:HASH:azerty17
user01_history18:HASH:azerty18
user01_history19:HASH:azerty19
user01_history20:HASH:azerty20
user01_history21:HASH:azerty21
user01_history22:HASH:azerty22
user02:HASH:99Monkey
user02_history0:HASH:00Monkey
user02_history1:HASH:01Monkey
user02_history2:HASH:02Monkey
user02_history3:HASH:03Monkey
user02_history4:HASH:04Monkey
user02_history5:HASH:05Monkey
user02_history6:HASH:06Monkey
user02_history7:HASH:07Monkey
user02_history8:HASH:08Monkey
user02_history9:HASH:09Monkey
user02_history10:HASH:10Monkey
user02_history11:HASH:11Monkey
user02_history12:HASH:12Monkey
user02_history13:HASH:13Monkey
user02_history14:HASH:14Monkey
user02_history15:HASH:15Monkey
user02_history16:HASH:16Monkey
user02_history17:HASH:17Monkey
user02_history18:HASH:18Monkey
user02_history19:HASH:19Monkey
user02_history20:HASH:20Monkey
user02_history21:HASH:21Monkey
user02_history22:HASH:22Monkey
user03:HASH:SomethingElse
user03_history0:HASH:Password0
user03_history1:HASH:Password1
user03_history2:HASH:Password2
user03_history3:HASH:Password3
user03_history4:HASH:Password4
user03_history5:HASH:Password5
user03_history6:HASH:Password6
user03_history7:HASH:Password7
user03_history8:HASH:Password8
user03_history9:HASH:Password9
user03_history10:HASH:Password10
user03_history11:HASH:Azerty$1
Usage example:
password-history-analysis.py passwords.txt
Output:
user01:24:24:100.00:azerty
user02:24:24:100.00:Monkey
user03:13:11:84.62:Password
The first field is the username.
The second field is the number of passwords for the given username.
The third field is the largest number of passwords for the given
username with the same prefix or suffix.
The fourth field is the percentage of third and second field.
The fifth field is the password's common string.
The report can be written to file with option -o.
Use option -l to convert usernames to lowercase.
Option -n will not produce a report, but output all lines that do not
match a password entry. Use this to detect entries not handled by this
program.
The separator (for input and output) is :, and can be changed with
option -s.
password-history-analysis_v0_0_1.zip (https)
MD5: 2ED7FB5E6968B25AEBF623754E5513B0
SHA256: DA75A8E2C92DCD31FB3C05732C660C3996EAEBADFA198535C051DC02AE94805B